SySense
Detect and Prevent Malware Execution in Firmware
Need
Problem: Firmware is on almost all modern devices, including phones, PCs, and internet-connected devices. When firmware is compromised, the operating system and applications within it can also be subverted. 57 CVEs were reported in 2023 for UEFI, the BIOS on modern PCs, including several that can be used to embed malware that persists across operating system reinstallation.
State of the art: Almost all vendors rely on code signing (Secure Boot on Intel).
Potential for failure: Code signing assumes that the vendor is trustworthy:
- the code is free of exploitable bugs,
- there are no malicious insiders,
- there is no possibility that their private key will leak, and
- that all of this is true of providers of third-party drivers.
Solution
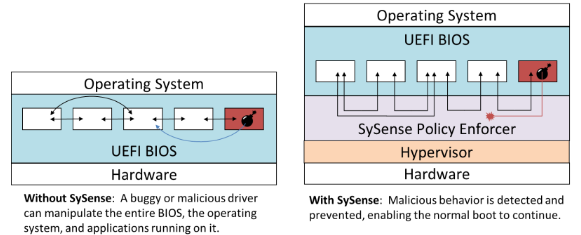
SySense determines what functionality each firmware driver requires and prevents it from abusing functionality it does not require, disabling most malware.
SySense uses a custom hypervisor to monitor firmware drivers, enabling them to access only necessary memory, files, and code. When a violation occurs, SySense automatically mitigates it, enabling normal execution to continue.
Benefits:
- Detects and prevents malicious behavior
- Records forensic information about violations
- Derives driver policies automatically in the high-level Tiffin language, with support for validation and editing by SMEs
- Negligible performance impact
System and Workflow
SySense in practice
Detects state-sponsored UEFI-based rootkits such as LoJax (Russia), and Cosmic Strand (China)
Detects malware exploiting CVEs such as LogoFail
Detects exploitation of 0-days
SySense for you
UEFI vendors can integrate SySense into their systems for best security and performance
SySense can load from a PCI card, enabling post-hoc security for tailored uses
SySense currently supports x86, but can be extended to ARM or other architectures upon request