INTRODUCTION:
The ISA/IEC 62443 standard (formerly ISA 99) is a set of process standards for secure development of products in industrial automation and control. A list of popular cyber security standards can be found at on Wikipedia. The IEC 62443 standard covers many aspects of security but of specific interest for software developers is Part 4-1 “Secure product development life-cycle requirements” which outlines a framework for security by design and defense in depth to guide the development of more secure industrial automation and control products. The standard makes specific reference to static analysis as a recommended tool or practice and this post outlines how advanced tools fit within the process requirements.
Related:

The Role of Static Analysis in Secure-by-Design Development Lifecycle
Static analysis tools like CodeSonar provide critical support in the coding and integration phases of software development. Figure 1 shows the overlay on a software development lifecycle for static and dynamic analysis tools. Ensuring continuous code quality, both in the development and maintenance phases, greatly reduces the costs and risks of security and reliability issues in software. In particular, it provides some of the following benefits:
- Continuous source code quality and security assurance: Detecting errors and vulnerabilities (and maintaining secure coding standards, discussed below) in the source code when initially developed yields the biggest impact from the tools.
- Tainted data detection and analysis: Analysis of the data flows from sources (i.e. interfaces) to sinks (where data gets used in a program) is critical in detecting potential vulnerabilities from tainted data. Any input, whether from a user interface or network connection, if used unchecked, is a potential security vulnerability.
- Third-party code assessment: Performing testing and dynamic analysis on a large existing codebase is hugely time consuming and may exceed the limits on the budget and schedule. Static analysis is particularly suited to analyzing large code bases and providing meaningful errors and warnings that indicate both security and quality issues.
- Secure coding standard enforcement: Static analysis tools analyze source syntax and can be used to enforce coding standards. Coding standards are good practice because they they increase the robustness and security of code.
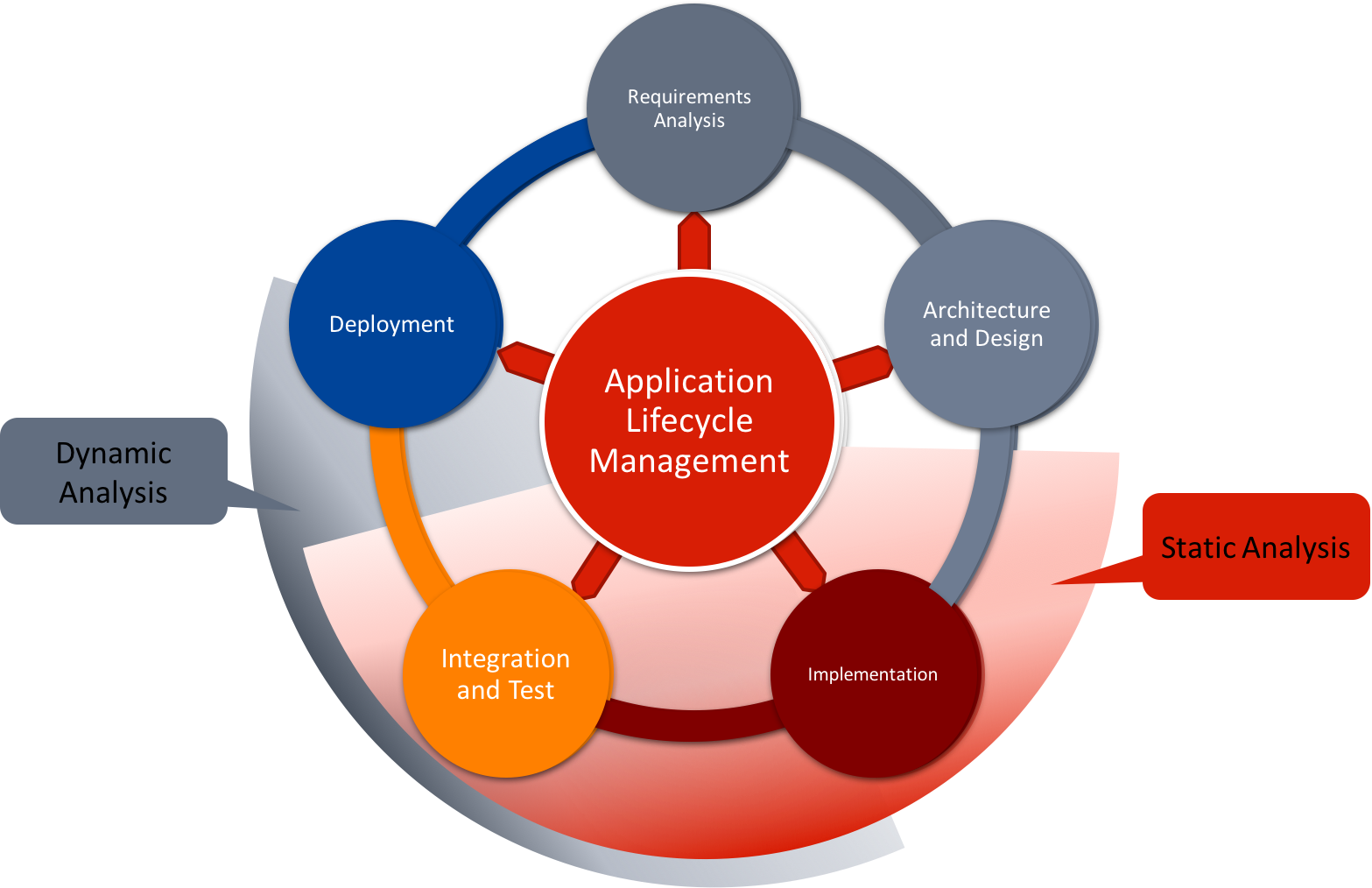
Figure 1: The role of dynamic and static analysis tools in a typical software development lifecycle.
Standard-Specific Guidance Regarding Static Analysis
The ISA/IEC 62443 standard emphasizes a philosophy of defense in depth (protection via multiple layers of defense leveraging multiple facets of security practice) with a secure-by-design approach. Figure 2 illustrates this philosophy.
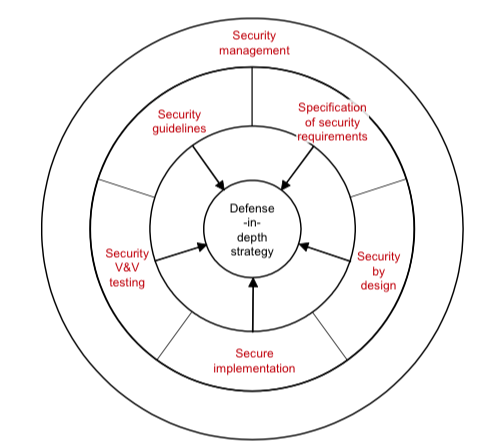
Figure 2: The security philosophy used in ISA/IEC 62443, defence in depth, secure by design.
Development tools, automation and static and dynamic analysis tools play a key part in “security guidelines” and “secure implementation.” The standard calls out the need for security expertise in both design and implementation but also in modern tools and techniques which include static analysis tools. In terms of secure implementation, the standard is very clear on the role static code analysis (SCA) tools play. The sections that call out SCA are noted below:
Security Expertise (Sec 5.5)
This section spells out the requirement for staff involved in development process having sufficient skills to perform their duties. The implication is that training is required where team members fall short. For example, this section states (Section 5.5.2):
Having this process means that personnel assigned to security-related processes have evidence that shows their relevant qualifications. This includes knowledge not only of security, but also for the use of any security-related standards (for example, coding standards), techniques (for example, best practices), and tools (for example, static analysis tools).
Third Party Embedded Component Security (sec 5.9.2)
The software supply chain is an increasing important security concern and this section calls out this specifically. Of interest here is the recommendation to evaluation third party software for security vulnerabilities using tools such as static analysis (Section 5.9.2).
This process is required to ensure that supply chain security is addressed for equivalent security practices, latest security updates, security deployment guides and the supplier’s ability to respond if a vulnerability is discovered.
…
c) employing compensating mechanisms for known vulnerabilities on COTS or open source components (such as static code analysis).
Secure implementation review (Sec 8.2)
Reviews and inspections are critical for reducing bugs and vulnerabilities. ISA/IEC 62443 addresses this directly in section 8.2. Static analysis (SCA) is called out directly:
A process shall be employed to ensure that implementation reviews are performed for identifying, characterizing and tracking to closure security-related issues associated with the implementation of the secure design including:
…
c) Static Code Analysis (SCA) for source code to determine security coding errors such as buffer overflows, null pointer dereferencing, etc. using the commonly defined coding rules for the supported platform. SCA shall be done using a tool if one is available for the language used. In addition, static code analysis shall be done any time the software is changed.
Then later in section 8.2.2:
In addition, manual source code reviews may be used to examine source code for adherence to best practices (see 7.6, SD-5 – Addressing security-related issues, and 8.2, SI-1 – Security implementation review), and automated static source code analysis may be used to identify anomalies, including security vulnerabilities in the code as well as non-conformities with given programming rules.
It’s clear that ISA/IEC 62443 is recommending good review practices that include manual and automated inspections assisted by static analysis tools.
Secure Implementation recommended practices (Sec 8.5.1)
During the implementation phase of the project, it’s critical to implement software as securely as possible. Secure coding standards and design rules that avoid unsafe practices is a required approach in ISA/IEC 62443. In particular, the implementation practices call out automated testing and static analysis (Section 8.5.1):
The implementation processes shall incorporate commonly accepted security recommended practices and coding guidelines that are periodically reviewed and updated and include at a minimum:
…
Automation plays a key role in successfully following these guidelines. Test automation that includes static and dynamic analysis increases the scope of error and vulnerability detection while decreasing overall workload.
CONCLUSION:
Static analysis plays an important role in ISA/IEC 62443 guidelines for implementing security in industrial automation and control systems. In fact, tools are specifically called out in key parts of the standard as recommended practices. GrammaTech CodeSonar advanced static analysis supports these requirements with additional benefits of improved general code quality, concurrency error detection, Application Lifecyle Management tool integrations and binary code analysis.
Like what you read? Download our white paper “How Static Analysis Protects Critical Infrastructure from Cyber Threats” to learn more.
{{cta(‘9682e3c6-546a-487a-9c34-d8b1cee8a4e4’)}}