
Over the years we have seen our customers “shifting left” to take advantage of building in security versus testing for security later in the lifecycle. As advanced SAST tools such as CodeSonar mature, we see that our customers are interested in three key areas of innovation: Safety and security is a primary area of risk management and they need their SAST tool to uncover as many potential liabilities as possible. It’s critical that SAST tools integrate with development environments to make the shift left transition as seamless as possible. In a similar vein, SAST tools need to be non-interruptive to their workflow – shifting left cannot slow down the development process.
In keeping with these key areas, we have announced version 6.0 of GrammaTech CodeSonar. Let’s take a look at some of the innovations in this new release:
GitLab Integration
CodeSonar integrates directly into the GitLab Ultimate CI pipeline to detect zero-day vulnerabilities. CodeSonar scan results are available in the GitLab Merge Requests, GitLab Security Dashboard and can be assigned as a GitLab Issue. Product development teams looking to shift left without disruption to their SDLC now have a seamless GitLab CI/CD integration.
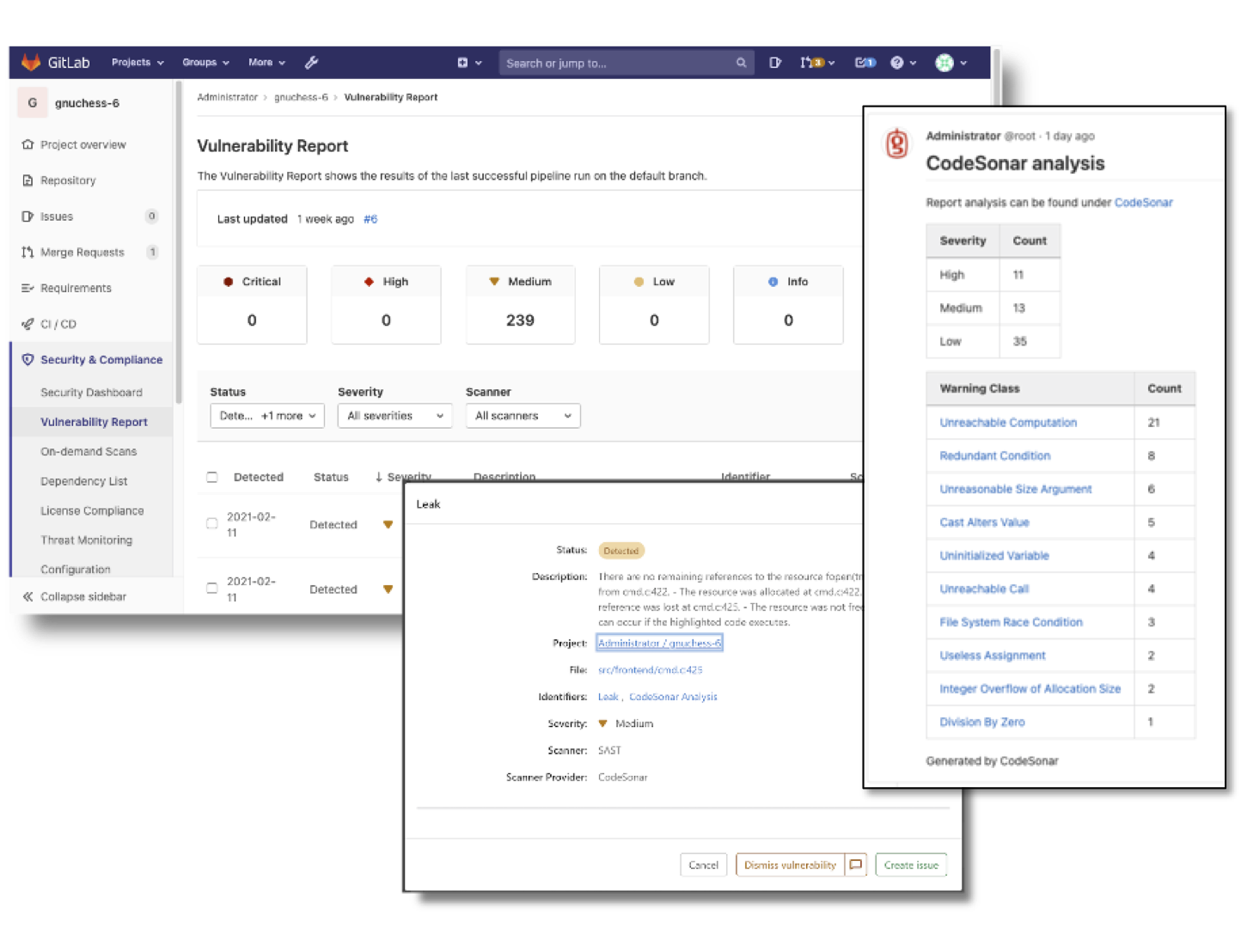
CodeSonar now enables developers to work with detected vulnerabilities right in the GitLab UI – you can review a warning, create a GitLab issue and assign it to a developer without ever leaving GitLab. In addition, you can dismiss vulnerabilities, and CodeSonar’s fingerprinting technology ensures that GitLab won’t ever show them to you again. CodeSonar warning message can be viewed directly in GitLab, and the detailed warning reports provided by CodeSonar with annotated source code is just a mouse click away – no copy and pasting or searching for line numbers.
DoD PlatformOne Ironbank Container
CodeSonar is now compatible and deployable as a DoD PlatformOne Ironbank container. Iron Bank is the DoD repository of digitally signed, binary container images that have been hardened according to the Container Hardening Guide. CodeSonar is now available to deploy in container form in conformance with the Ironbank requirements.
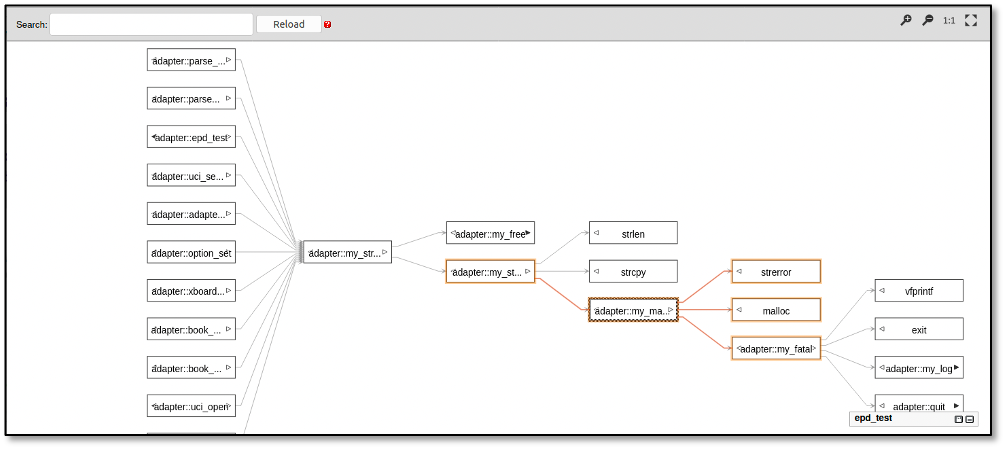
Improved Warning Code Visualization
Visual representation of warnings helps developer both understand the root cause but also helps them fix the detected bug easier. CodeSonar has improved the visualization capability, compatible with all major web browsers, when investigating warnings to help reduce the remediation time for warnings.
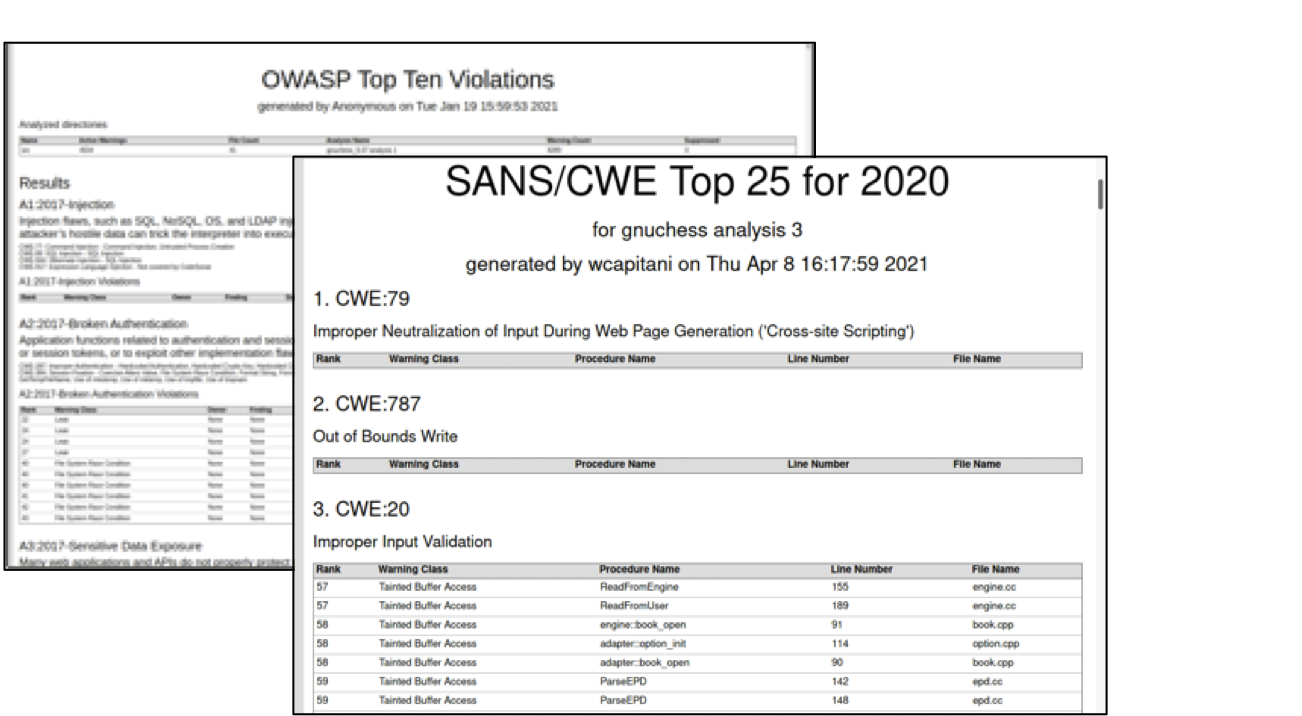
New Built-in Security Reports
CodeSonar now includes built-in security reports to make it easier and faster to understand what vulnerabilities are present in your software projects. You can now generate a report of the OWASP Top 10 (2017) and SANS/CWE Top 25 (2020) vulnerabilities detected in your analysis. These reports can be used immediately on existing CodeSonar projects, or customized to meet the needs of your organization.
Improved Static Analysis
In the latest version of CodeSonar we’ve added a new format string checker to detect missing or incorrect arguments to format string function calls. This new checker is aimed at CWE-628 Function Call with Incorrectly Specified Arguments software weakness.
This release also includes more a more detailed CWE reporting with a refined mapping between CodeSonar warnings and CWE identifiers.
Unified Java Language Support
This release of CodeSonar sees the full integration of the Julia analysis engine. The same user experience is provided for all supported languages: C, C++, and Java. This updated Java support includes broad support for Java-related CWEs. Also included is support for Android 11 to help improve the quality and security of Android applications.
New Compiler and C++ Feature Support
The latest version of CodeSonar includes updated support for GCC 10, IAR and Clang 10 compliers and we have added support for the new ARM Clang complier.
This release includes support of 20 new C++ language features – proactively ready for when our customers start using the new libraries and frameworks.