FVA – FPGA Vulnerability Analysis Tools
Assess FPGA designs for vulnerabilities throughout their lifecycle
Need
Modern hardware platforms rely on FPGAs with advanced designs and complex third-party IP. Vulnerabilities can be introduced into these designs through third-party IP, malicious design modification, configuration data at rest, or even the automated tools used to create the designs.
Hardware analysts need tools to help them identify and eliminate vulnerabilities, with maximum automation and minimum need for expertise.
Very few such tools exist today, and those that do have limited functionality and depth of analysis.
Solution
FVA is a state-of-art FPGA design analysis platform that is powerful today and extensible for the future. It provides:
- Automated reverse engineering of unknown designs to a netlist or configuration file
- Automated vulnerability analysis, including detecting Trojans and identifying their location
- Computation of vulnerability metrics to quantify design security
- Intuitive GUI to view and interact with results, as well as programmatic API
- Design rewriting capability for hardening assurance techniques
- A platform for the development of new analyses
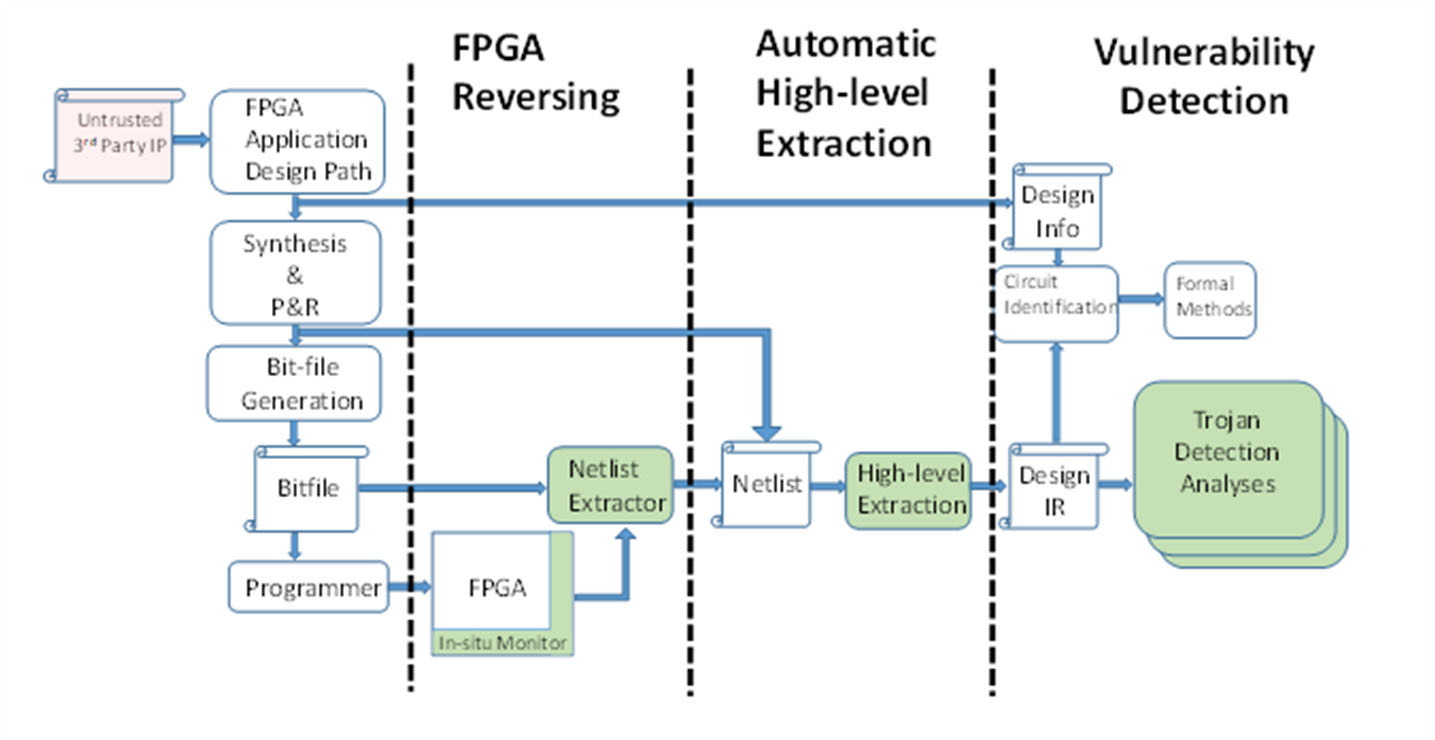
System and Workflow
FPGA Reversing: Start with implementation netlist or use Bits2Netlist to get a physical netlist. If the netlist and/or design info are already available from the design process, they can be plugged in directly rather than reverse-engineering.
Automatic High-Level Extraction: Understand structure, IP, state-machines, functions, etc.
Vulnerability Detection: Perform a configurable suite of design analyses on extracted information.
FVA in practice
We benchmarked FVA on a suite of Trojan testbench designs and full-scale FPGA designs.
-
Largest design analyzed: OpenTitan, a Xilinx FPGA SoC implementation of Root-of-Trust
(RoT). Uses more than 128,000 LUTs in a Xilinx Virtex 7 - Analysis time: 10-20 minutes (average), six hours (very large designs like OpenTitan)
-
FVA outperformed existing vulnerability detection metrics for Trojans:
- Dramatically reduced false positives
- Gave clear identification of Trojan, including location
FVA for you
FVA is available as Linux software and libraries. It includes both graphical and command-line
interfaces, a Python API, and Xilinx part support data.
We can assist with custom enhancements by developing:
- Libraries for specific applications or ASIC/FPGA technologies
- New analyses for reverse-engineered designs.
This material is based upon work supported by the Office of Naval Research (ONR) under Contract No. N00014-21-C-1032. Any opinions, findings and conclusions or recommendations expressed in this material are those of the author(s)and do not necessarily reflect the views of the ONR.
DISTRIBUTION STATEMENT A. Approved for public release: distribution unlimited. Approved, DCN#0543-2419-24