Proteus
Empowering Cybersecurity Through Automated Vulnerability Discovery and Remediation
Proteus is an advanced software testing system for automatically finding and fixing vulnerabilities, with no false alarms, aimed at development groups, testing organizations, and cybersecurity teams. It discovers vulnerabilities that could be triggered by potentially malicious file or network inputs, including many common entries in the Common Weakness Enumeration (CWE). The tool supports Windows and Linux native binaries.
Need
Current cybersecurity processes are inefficient, requiring countless expert-hours to identify and mitigate vulnerabilities, yet cyberattacks continue to succeed. The severe shortage of experts and overwhelming volume of work pose significant risks to critical infrastructure and software systems.
The state of the art in automated cybersecurity includes fuzzing, symbolic execution, error amplification, binary rewriting, exploitability analysis, binary patching, and hardening.
Existing practical solutions often fall short in efficiency and coverage, leaving critical vulnerabilities undiscovered and unmitigated.
Solution
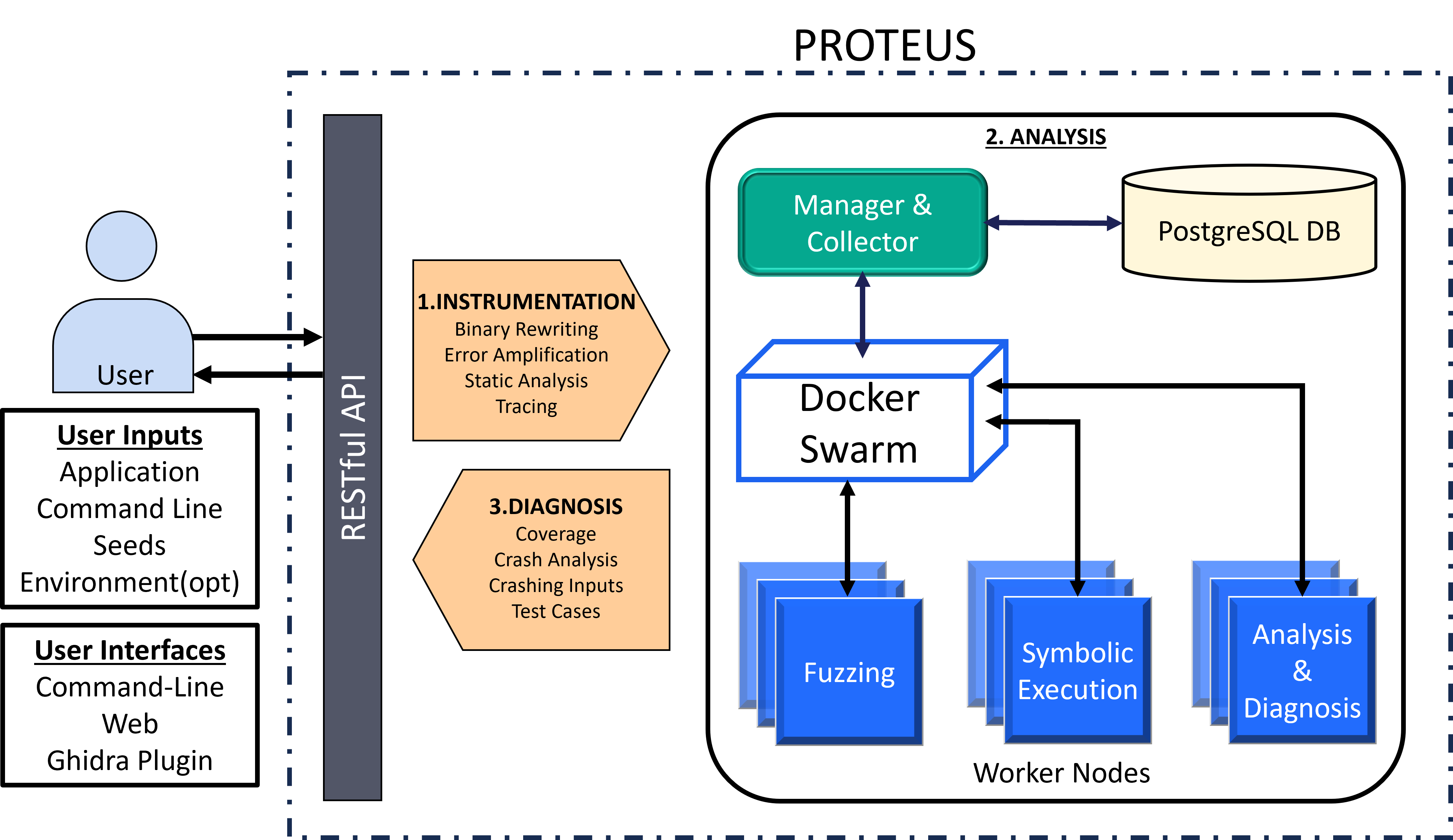
Proteus automates the discovery and remediation of software vulnerabilities operating directly on binaries, eliminating the need for source code. Proteus effectively identifies vulnerabilities and provides remediation strategies by leveraging symbolic execution, fuzzing, runtime monitoring, error amplification, and exploitability analysis.
Benefits:
- Automate the detection and patching of vulnerabilities, reducing the manual effort required
- Improve security posture by identifying and mitigating vulnerabilities that would otherwise remain unnoticed
- Reduce operational costs by lowering the time and resources dedicated to vulnerability management
System and Workflow
Proteus in Practice
- DARPA Cyber Grand Challenge 2016: Proteus ranked 2nd in the DARPA CGC 2016 and has since matured through efforts with the Defense Innovation Unit (DIU) and other military branches
- DoD Customer Transition: In 2021, Proteus was transitioned to a major DoD customer, where it was successfully applied to a complex mission planning system. Proteus automatically identified and remediated vulnerabilities in native x86 binaries, demonstrating its capability to enhance security for mission-critical systems
- Magma Benchmarks: On Magma benchmarks, Proteus doubled the number of crashes found compared to conventional fuzzing methods
- DARPA AIxCC 2024: Proteus is the foundation of GrammaTech’s solution for DARPA AIxCC, showcasing its advanced capabilities in automated vulnerability detection and remediation
Proteus for you
- Business Model: Proteus is tailored to meet diverse organizational requirements, offering flexible deployment models including on-premises leasing.
- Government and Tactical Use: Recognized for its robust security features, Proteus has achieved Authorization to Operate (ATO) and is also available for air-gapped environments, making it an ideal solution for classified settings where secure, isolated operation is crucial
- Guided Threat Analysis: For organizations seeking expert analysis, Proteus provides Guided Threat (GT) services. Our team of cybersecurity experts utilizes Proteus’s advanced capabilities to conduct thorough analyses, offering detailed insights and recommendations tailored to your unique security posture.
- Open Source Version: Plans are underway to release an open-source version of Proteus with limited capabilities following the completion of the AIxCC project. This will broaden access and engage the community in its ongoing development. Details and a link will be provided upon release.
This material is based upon work supported by the U.S. Air Force, DARPA, the U.S. Army, DIU, the U.S. Navy and the U.S. Office of Naval Research under Contract(s) No. FA8750-14-C-0110, W15QKN-18-9-1013, W56KGU-17-C-0028, FA8750-15-C-0113, HR0011-18-C-0061 and N68335-17-C-0700. Any opinions, findings and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the Air Force, DARPA, Army, DIU, the Navy or the Office of Naval Research.