
We have discussed the benefits of using SARIF, an open standard for exchanging static analysis results, in a previous post. Integration between tools is simplified by using this open standard for data interchange between tools. GrammaTech has a proposed modification to Clang to support output from its built-in static analyzer (Clang SA). We can then use the SARIF output and integrate Clang SA results into CodeSonar.
What is the Clang Static Analyzer and where is it Useful?
The Clang SA is a source code analysis tool that finds bugs in C, C++ and Objective-C code. It runs as a stand alone tool or inside Apple’s Xcode IDE. The Clang SA (excluding Xcode for our purposes) is executed at the command line using the scan-build command that uses the Clang language processor underneath which provides the source analysis. Clang SA provides a free and easy way to check C/C++ code for bugs before submitting code to source control, before a build and the start of unit testing. As with any static analysis tool, finding and fixing bugs early, pays off.
During the Clang SA invocation with scan-build the user can specify the output format as SARIF, for example, creating an output file of all the warnings found. The SARIF file can then be imported into any supporting tool.
The Clang SA provides good coverage of common C/C++ errors and some security vulnerabilities and it is provides results fast, making it easy to integrated as part of every build. Clang SA differs from commercial solutions, such as CodeSonar, in two main areas.
- Commercial tools like CodeSonar check for more types of problems and scan deeper using a model of the whole program including inter-procedural and context and path sensitive analysis. A good summary as to why recall is important is this blog post.
- Enterprise features. Clang SA is a tool for use by a single developer and it provides it’s warnings much like compiler warnings. Commercial tools like CodeSonar track warnings across builds, allow teams to comment on them during the review process, and often provide advanced code navigation capabilities as well to resolve warnings quicker.
If interested in more details on the comparison between advanced static analysis and various free and open source tools available, see our whitepaper “Advanced Static Analysis for C/C++.”
How do Clang SA and CodeSonar Work Together?
The SARIF format provides all the required detail to describe, display and help fix the warnings that are found. CodeSonar can import the Clang SA generated warnings into the same database as its own warnings. By doing so, developers can access the warnings in an organized fashion, organized by various criteria such type, severity and location by file. The integration into CodeSonar’s web portal provides the same types of information as a CodeSonar-generated warning with the ability to assign, prioritize, change state, etc. The warning is overlaid on the source code allowing for root cause analysis and determination of true versus false positive status. See the example screenshot from CodeSonar using imported warnings via SARIF from Clang SA performed on Objective-C code.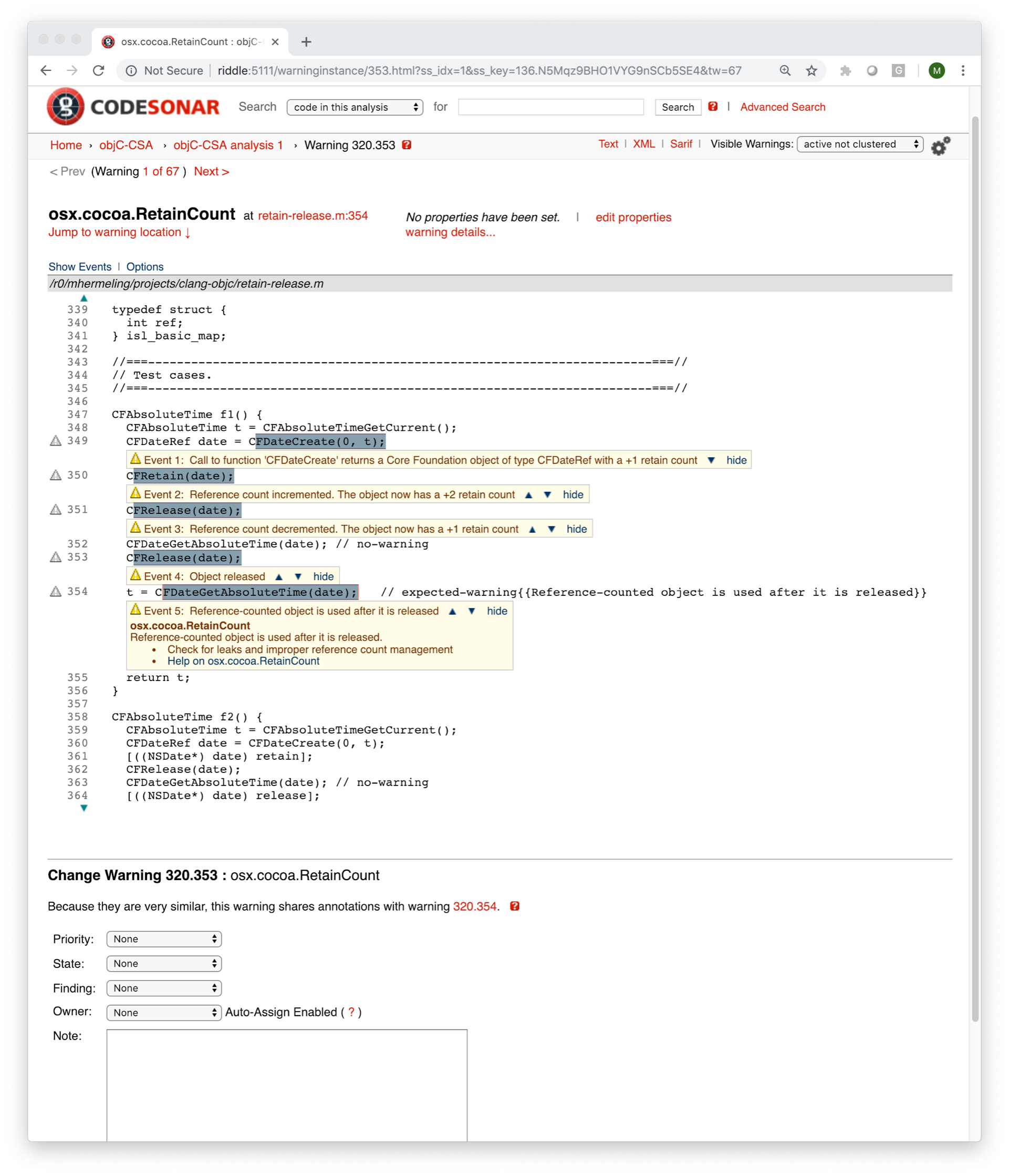
Here’s another example of an imported warning from Clang SA in C/C++ code:
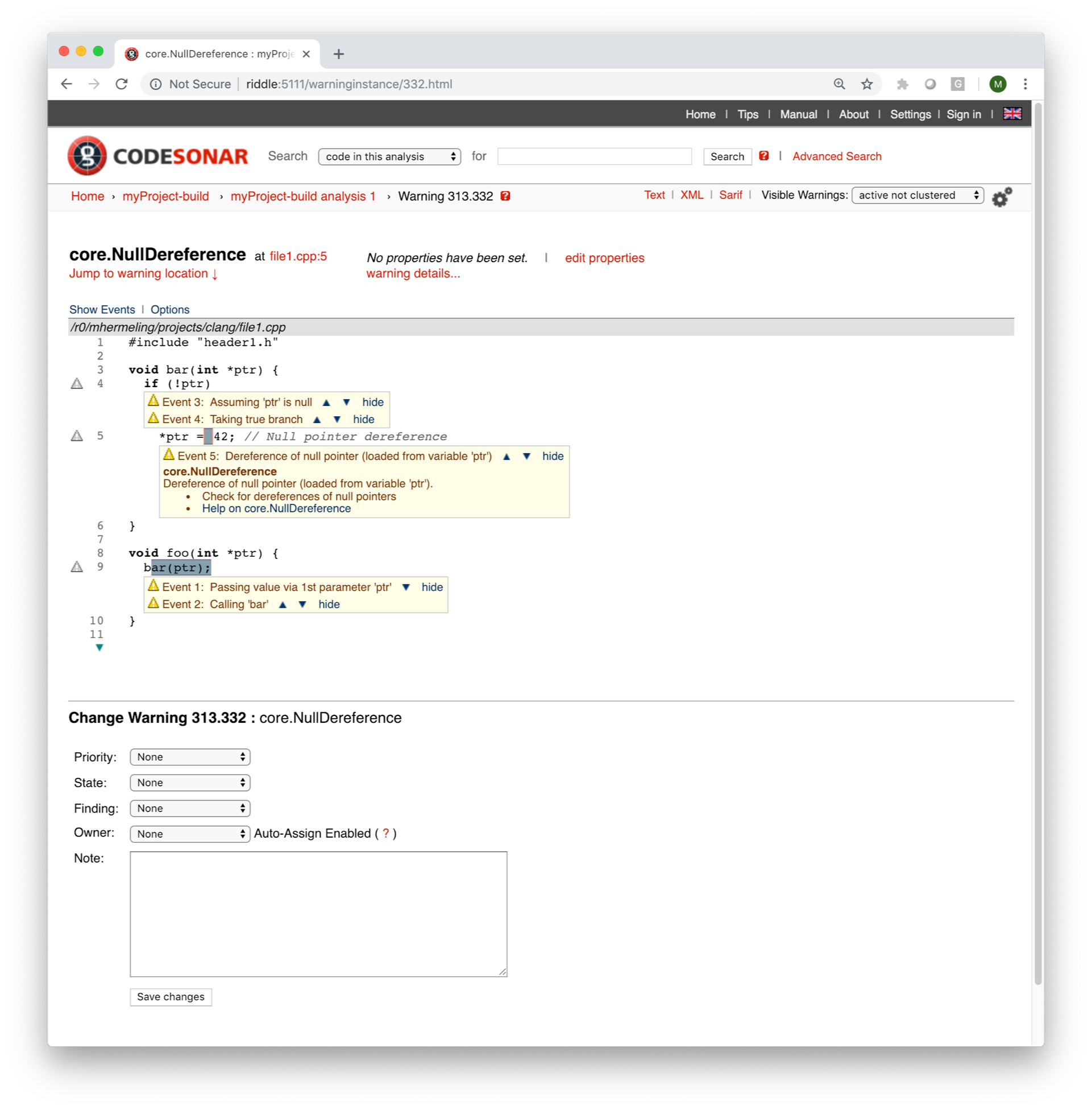
As can be seen, any SARIF imported warnings, including those from Clang SA can be managed in the same way as native CodeSonar warnings. A software development team could use Clang SA at the developer’s desktop for a quick code sanity check and then use CodeSonar on full project during the regular build cycle. Results of both of these analyses are manageable from the same interface.
Summary
The Clang Static Analyzer provides quick (and free) analysis of C/C++ source code, finding many common C/C++ bugs. Although predominately a command-line tool, it’s output can be used with other tools when using the SARIF output format. CodeSonar supports SARIF and Clang SA output, allowing for display and management of warnings in the same fashion as those generated by CodeSonar itself. The ability to manage the warnings adds value to teams looking to integrate developer-desktop analysis results with larger, project-wide results from CodeSonar.
Interested in learning more? Read our guide on “Advanced Static Analysis for C++”
{{cta(’42fd5967-604d-43ad-9272-63d7c9d3b48f’)}}