In July 2017, one of the biggest data breaches was due to an insecure and out-of-date web application platform. This breach would have been prevented if the Apache Struts platform the web application ran on had the most recent updates applied. This is of course, the massive Equifax breach which impacted over 145 million customers. The vulnerability used to expose the data had been discovered in March of 2017 and the attack on Equifax started in May but was not disclosed until July. In hindsight, it became an example of how important it is to secure the software supply chain.
Major Security Incidents are Expensive
Data breaches and other high-impact security incidents are expensive. So much so, it’s surprising that many of the affected companies only change their security posture after an attack has been made public. For example, data breaches affecting small and medium-sized businesses cost an average of $114,000 whereas on an enterprise scale, they can cost, on average, $1.2 million (2018 data, Source: Kaspersky Labs).
In another report, Kaspersky points out, one of the key ways to prevent data breaches is to patch and update software. It’s a fairly straightforward solution but first requires an organization to be aware of potential security risks. Understanding the composition of all your enterprise software, including infrastructure components, is key to evaluating an overall security risk. This is an area where software composition analysis (SCA) can help. But how do you know when to patch software if the source code is unavailable to you? Many of the 2nd and 3rd party components that make up your software stack have these “known” vulnerabilities that are “unknown” to you. How do you ensure that this code does not contain vulnerabilities? A new class of SCA offerings – that can determine vulnerabilities in 2nd and 3rd party software components have emerged – Binary SCA.
Binary Software Composition Analysis Beyond Application Software Development
The most common usage of SCA tools is by software teams vetting their open source and third-party software as part of the security practice. SCA tools, however, such as GrammaTech CodeSentry, aren’t exclusively software development tools. Many of the software operations in an enterprise are outside the scope of the software development teams.
Is the deployed web infrastructure considered as part of the software supply chain during development? It should be, but it’s easy to see that application developer could assume that the IT department is responsible for securing the website. Of course, these are the types of silos that DevSecOps tries to break down but that’s not a reality in every enterprise. There is also the issue of existing and legacy applications that predate modern security practices.
Any enterprise is only as secure as its most insecure application, thus it’s important to consider the scope of security analysis beyond current software development. SCA tools using binary analysis can help organizations understand their true software bill of materials (SBOM), even when source code isn’t available, and the security vulnerabilities associated with each component.
CodeSentry Binary Analysis
CodeSentry uses deep, scalable binary analysis to create a detailed software bill of materials (SBOM) and lists known vulnerabilities in the detected components, including any dependencies. CodeSentry continuously tracks these vulnerabilities throughout the software lifecycle. The SBOM can be embedded along with each application making audit requests more reliable. The type of analysis used yields high precision and recall meaning less missed vulnerabilities and less false positives.
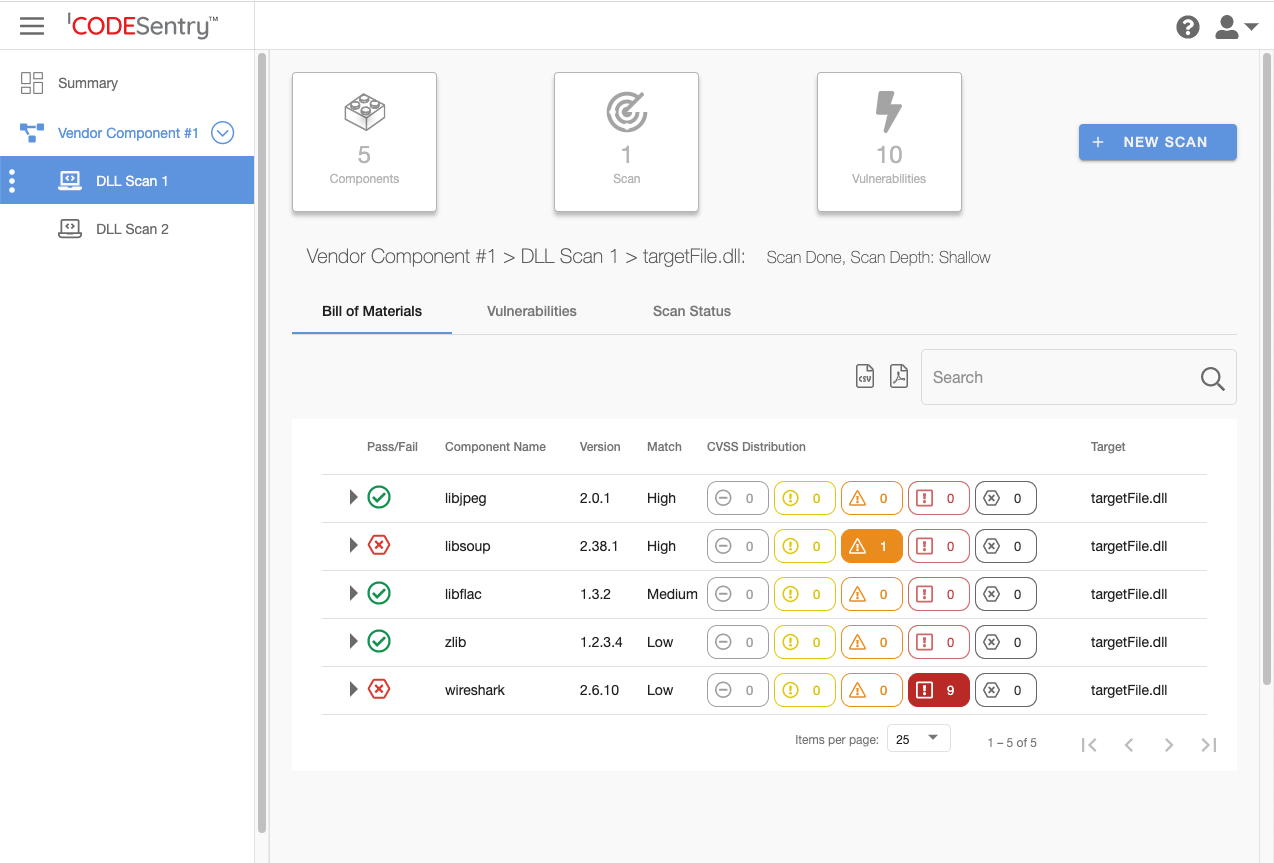
An example SBOM from CodeSentry
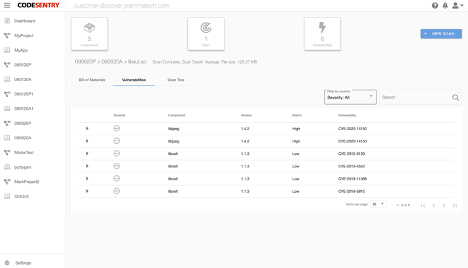
An example vulnerability list from CodeSentry
The advantage of binary analysis in creating a comprehensive SBOM is that source code isn’t required. The binary analysis also provides a more complete picture of the components, dependencies and vulnerabilities. Detected vulnerabilities can be assessed on a risk and impact basis and spur on software updates and even changes in components as needed.
Summary
Securing the software supply chain needs to extend beyond just current development projects into all operating software across the enterprise. As companies move to more sophisticated security practices it’s important to consider existing and legacy systems and the risks associated with them. This is particularly true for public-facing applications and the associated platforms they run on. Binary software composition analysis is uniquely suited to provide a comprehensive SBOM along with known vulnerabilities in open source, third-party software, and all related dependencies. The SBOM generated by GrammaTech CodeSentry can be used to drive and justify security improvements in the software supply chain.
