
Android is, for most people, a mobile operating system for their phone or tablet. In fact, it’s an extremely successful open source platform in general. It’s common in automobile infotainment systems, set top boxes and even finds its way into industrial uses. From the user’s perspective it’s an easy-to-use user interface with a common set of capabilities making it easy to move from one device to another. For manufacturers, it’s a platform that consists of both the Java-based Android sand-boxed operating environment and an embedded Linux operating system running on hardware. Below the Android virtual machine, the product relies on C/C++ programming, drivers and libraries and various other realities of embedded development. In a mixed environment it’s important the tools used for security improvement support the software stack.
Security Issues with Android as the Application Layer
Android had the dubious distinction of being the most insecure OS of 2019 (data in this report used NIST’s NVD.) The common weakness enumeration has a specific category Weaknesses in Mobile Applications which summarizes the top software issues that lead to vulnerabilities at the Android application level. At this level, the most common weakness is exposure of sensitive (personally identifiable) information and related issues such as poor encryption or hard-coded credentials. Many of these types of issues can be detected with static analysis tools such as GrammaTech CodeSonar for Java.
CodeSonar for Java – Building in Better Privacy Protection
Protecting sensitive data is a top priority when it comes to information management. Most Android developers deal with PII and payment data, and its quantity is increasing day by day. Data protection is an organization-wide issue, and achieving it requires efforts from all internal groups . All applications should be created following the “Privacy by Design” principle, to make sure that treatment of sensitive data is handled correctly from the beginning. To verify legacy software, and support the development of new applications, a thorough understanding of how sensitive data is handled is paramount. The sophisticated tainted data analysis provided by CodeSonar for Java allows developers to understand where external data is being stored and where that stored data is used in the application.
Sophisticated data flow analysis traces critical data from source (where it enters the application) to “sink” (where it gets used.) If potential exposure is detected along this flow, a warning is issued. Combining this analysis along with coding rules that warn of potentially insecure coding constructs, eliminates these security vulnerabilities during development.
Security Issues with Android as an Embedded Platform
The most notable security vulnerabilities with Android are at the application level. However, there are security issues that plague the embedded Linux layer of Android products. At this level, the platform is subject to the same attacks and suffers the same weaknesses of any embedded Linux product. In a recent case, Samsung patched the Linux kernel on their own which ended up creating a larger security issue.
Unfortunately, the next most insecure operating system in 2019 was Debian Linux which implies the security of the embedded platform underneath the Android can’t be assumed. Many of the Linux vulnerabilities are in the kernel itself which isn’t something that gets updated regularly on Android platforms. In addition, there are vulnerabilities in libraries and services commonly running on Linux that can be exploited by hackers. The Heartbleed vulnerability in OpenSSL applied to devices running Android 4.11, for example. Luckily, this vulnerability was isolated to this version and Google quickly patched it.
Software Composition Analysis for Embedded Linux Platforms
It’s unlikely that platform developers for Android devices are going to use SAST tools on the entire Linux kernel and all associated libraries. It’s a large amount of complex code and any issues found will not be easy to remediate without deep knowledge of the Android code base. On the other hand, using Software Composition Analysis (SCA) makes more sense for open source and other third party components of the platform.
GrammaTech CodeSentry uses binary analysis to build a complete software bill of materials (SBOM) and and vulnerability report, referencing the National Vulnerability Database (NVD). This provides Android platform developers with a complete list of components and known N-day vulnerabilities. Including SCA into the regular build and deployment process means that detected vulnerabilities are tracked over time and as new components are detected and new vulnerabilities arise, the team is notified in the updated SBOM and vulnerability report.
SAST for Custom Code
Where static analysis tools, like CodeSonar, will make sense in Android platform development is for custom code on the embedded platform, usually in C/C++, where the source is available for analysis and the development team is responsible and familiar with the code. It is at this level that security issues can be eliminated in the deployed product by using a combination of prevention and detection. Prevention comes from using good coding practices that avoid software weaknesses in the first place. Standards such as SEI CERT C, for example, provide comprehensive guidelines for writing more secure code and SAST tools can be used to enforce these standards. Detection comes from using sophisticated analysis capabilities of SAST tools to detect security vulnerabilities in the code already written. These two approaches go hand in hand in preventing security vulnerabilities at the platform level.
To summarize the importance of Static Application Security Testing (SAST) tools like GrammaTech CodeSonar in improving software security, it provides some of the following benefits:
- Continuous source code quality and security assurance
- Tainted data detection and analysis to uncover complex security vulnerabilities
- Detect complex issues that are obfuscated and span process/file boundaries
- Secure coding standard enforcement
SAST and SCA tools can be used together throughout software lifecycle although their respective strengths are more useful at different phases. As the diagram below illustrates, SAST plays a role through the develop-build-test phases for custom code and SCA applies on the third-party code and software supply chain:
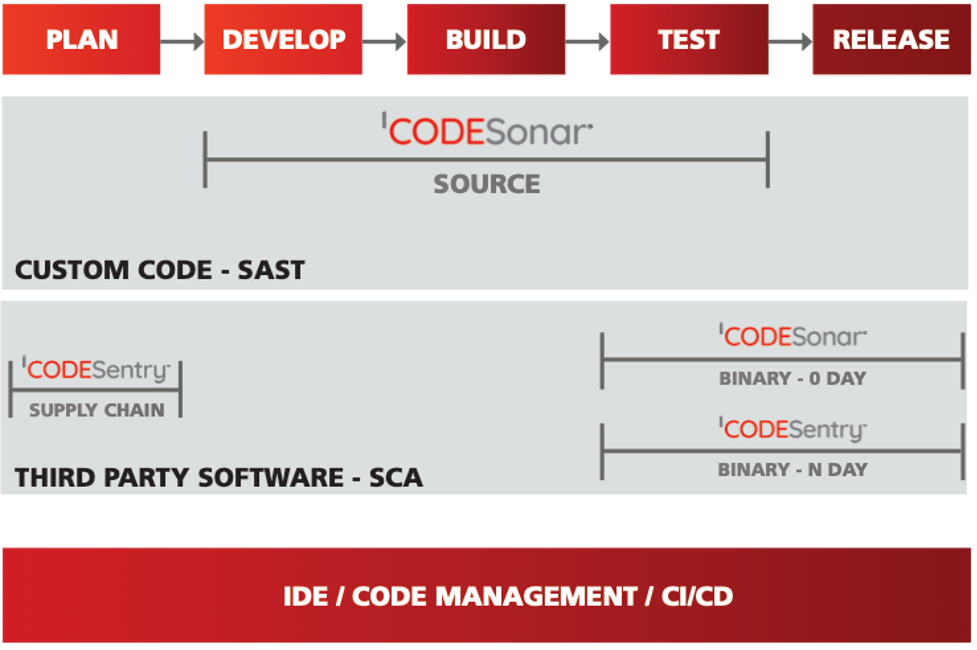
Summary
Android remains one of the least secure operating systems in popular use. Most of the security issues exist at the application level in Java apps running on top of a virtual machine. Android platform developers, who are developing Android-based devices and the hardware it runs on, are dealing with security concerns at multiple levels. They need to be concerned with security at both the application level and within the embedded Linux platform which runs on the device hardware. There are security issues at both layers and although the nature of them differs, neither can be overlooked.
To help with this situation, modern SCA and SAST tools provide multi-language support for languages used at the different layers of an Android platform. SCA tools are better suited for open source and third party software to create a complete SBOM and report of known vulnerabilities. SAST tools are better suited for code development at the application level (in Java) and the embedded platform level (in C/C++). Using a combination of these tools means that Android platform developers can cover all the bases for improving security.